Beacons in Citrix StoreFront are being used to detect if the user is trying to access the store from a local or public network. When doing Virtual App and Desktops implementations I like to configure a single FQDN setup for the Citrix Gatway and the StoreFront URL (Example: https://citrix.company.com). With this URL the end users will always be able to launch their published resources doesn’t matter if they are located inside the company or surfing via a public Wifi. The default setting is that the internal beacon URL is the service URL specified in the Citrix StoreFront console.
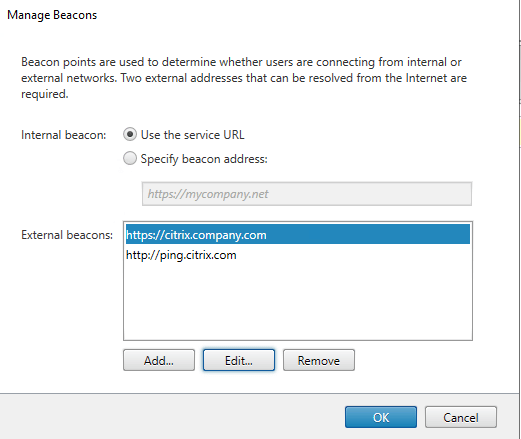
This is going to be a problem if we want to achieve a true Single FQDN setup. We need to point the internal beacon to a different URL which is high available otherwise the Self-Service will stop working and the users are not able to launch their applications and desktops anymore.
At this state we have two possibilities to configure the beacon:
Option #1 – Easy Approach
– Create a DNS A-Record and point it to the StoreFront Load Balancer VIP
Example: citrixbeacon.company.com -> 192.168.2.130
– Internal Beacon is configured to https://citrixbeacon.company.com
(Note: The beacon traffic can go over HTTP or HTTPS – Just make sure the Common Name/DNS attribute of the SSL certificate is matching otherwise it will not work)
This is the most easy configuration. But it will not work in all environments. I have seen some customer where the external DNS is responding to all kind of A-records even if they are not registered. Let me show you what I mean:


We have not registered “123456.company.com” neither “citrixnotavailable.company.com” in our DNS server but they are getting resolved which is bad for our intention. With this behavior the beacon detection will simply not work and we need to operate with a DNS domain which is only resolvable inside the corporate network. Thats where I came up with the idea to use the Citrix ADC to create a high available beacon/network detection service which is independent from the Citrix StoreFront Load Balancer.
Option #2 – ADC Approach
We are goint to create a Load Balancing vServer which is responding with a simple HTML page. This is how the end result will look like:

Configuration Steps
1.) Create a HTML Page (AppExpert >Responder > HTML Page Imports)

2.) Create a Responder Action & Policy


3.) Create a LB vServer and bind a dummy “Always Up” service + responder policy
4.) Create a DNS-Record for Network Detection Service
5.) Configure the StoreFront Beacon


Nice man
Would love to see some more detail on step 3, “Create a LB vServer and bind a dummy…”.
Hello Jesse. This should help:
add service svc_AlwaysUp 127.0.0.1 HTTP 80 -gslb NONE -maxClient 0 -healthMonitor NO -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp OFF -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
bind lb vserver lb_vsrv_storefront-beacon_http_80 svc_AlwaysUp
bind lb vserver lb_vsrv_storefront-beacon_http_80 -policyName resp_pol_internalbeacon -priority 100 -gotoPriorityExpression END -type REQUEST
On the second line I’m getting:
ERROR: No such resource [name, lb_vsrv_storefront-beacon_http_80]
Where/when was I supposed to create a service called lb_vsrv_storefront-beacon?
Make sure to create the LB vServer before binding any services or policies.
Any chance to see this in GUI form like the above.
Would love to see more detailed instruction on how to create each step. It is very confusing if you try to configure with less detailed steps. Not all of us are Citrix Gurus.
Where should point this DNS-Record for Network Detection Service (127.0.0.1) or some other ip?
When I try to create that html Page (AppExpert >Responder > HTML Page Imports) I get this “Problem in importing the objects. Please check the DNS nameserver/router settings and try again. For more detail see /var/log/ns.log file. Any help would be greatly appreciated
Hello Wesley. Hope this helps:
1.) For creating the HTML object. Go to System –> AppExpert –> Responder –> HTML Pages
Name: internalbeacon
Import From: Text
2.) The DNS Records needs to point to the VIP of the Load Balancing vServer. Check the comment from 20th of April. There you will find the CLI commands.
Julian
Hello Julian,
Apologizes for my late response, but been crazy busy these days.
Just want to say a BIG Thank you for providing more detailed explanation to my question and solution.
I want to ask another question in relation to Load Balancing vServers, as I’m trying to learn this technology.
I have created Load Balancing vServer (20.20.10.11) for our 2 StoreFront servers.
I use the same URL name (myapps.mycompany.com) for both external and internal access.
Our Netscaler is in DMZ subnet and we use single arm configuration.
My LB vServer IP is in 20.20.10.0 /24 subnet and my internal LAN IP subnet is 172.16.5.0 /24
My 2 StoreFront servers have 172.16.5.100 and 101 IP addresses assigned accordingly and my internal DNS URL myapps.mycompany.com is pointing to those two IPs. Which means is using Round Robin DNS for balancing the load.
So, my question is.
Do I tell my Internal DNS to use LB vServer IP (20.20.20.11) to resolve myapps.mycompany.com URL for my Internal users when they access StoreFront Portal?
Hopefully I’m explaining myself here correctly, but if you need more details then please let me know.
I really appreciate your time and help to provide me with some guidance.
Cheers,
Wesley
Hello Wesley, from a security perspective it is recommended to separate the zone DMZ & LAN to dedicated ADCs. You have various options here.
#1: If your environment is not to big just work with VPX Freemium in the LAN. This will give you 20Mbit with no extra costs. Host the SF LAN VIP on this ADC and point the DNS Record to it.
#2: Take a look at Traffic Domains. This will allow you to separate DMZ/LAN (same ADC) with some limitations.
#3: Just use the DMZ VIP (not recommended)